Here is a useful SSL (HTTPS) application for anyone with a remote Linux server they want to keep an eye on using Blynk and the NodeMCU ESP8266. This little app also works (have tested as well) on the WeMos D1 ESP8266 Arduino board.
The NodeMCU setup could not be easier, just find a suitable mini-USB cable and plug it in
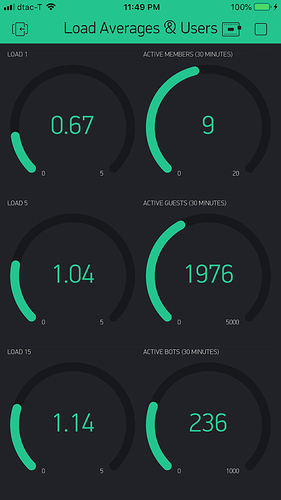
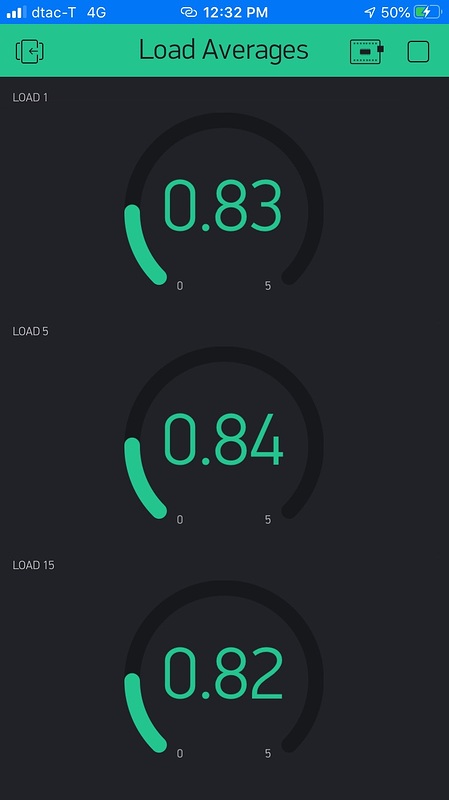
The Blynk app (running on aniPhone) looks like this:
Here is the Arduino sketch, which requires the ESP8288 board manager lib:
https://arduino.esp8266.com/stable/package_esp8266com_index.json
and you also need to install the Blink and the ESP8266 libs in your Arduino IDE (I assume you can do these tasks, if not please reply and ask).
Here is the Arduino sketch. You will need the SSID of your WIFI network and the password (if any) and your Blink app auth code:
/*************************************************************
This Arduino sketch is for the NodeMCU ESP8266 v0.11
The code makes an GET request to a remote Linux server PHP API using SSL
and GETs the Linux load averages as a simple string, parses the
string in a very basic way display the results on a Blynk apply
using virtual pins v0, v1 and V2.
The entire sketch should be rewritten to use JSON.
Use anyway you wish, freely and at your own risk of course.
Neo https://www.unix.com January 31, 2020
v0.11 removed delay(2000); //GET Data at every 2 seconds per PeteKnight
https://community.blynk.cc/t/blynk-project-nodemcu-esp8266-ssl-application-for-linux-server-load-averages/43305
Download latest Blynk library here:
https://github.com/blynkkk/blynk-library/releases/latest
Blynk is a platform with iOS and Android apps to control
Arduino, Raspberry Pi and the likes over the Internet.
You can easily build graphic interfaces for all your
projects by simply dragging and dropping widgets.
Downloads, docs, tutorials: http://www.blynk.cc
Sketch generator: http://examples.blynk.cc
Blynk community: http://community.blynk.cc
Follow us: http://www.fb.com/blynkapp
http://twitter.com/blynk_app
Blynk library is licensed under MIT license
This example code is in public domain.
*************************************************************
This example runs directly on NodeMCU.
Note: This requires ESP8266 support package:
https://github.com/esp8266/Arduino
Please be sure to select the right NodeMCU module
in the Tools -> Board menu!
Change WiFi ssid, pass, and Blynk auth token to run :)
Feel free to apply it to any other example. It's simple!
*************************************************************/
/* Comment this out to disable prints and save space */
#define BLYNK_PRINT Serial
#include <SPI.h>
#include <ESP8266WiFi.h>
#include <BlynkSimpleEsp8266.h>
#include <WiFiClientSecure.h>
#include <ESP8266HTTPClient.h>
#include <ArduinoJson.h>
BlynkTimer timer;
// You should get Auth Token in the Blynk App.
// Go to the Project Settings (nut icon).
char auth[] = "YOUR_BLYNK_AUTH_CODE";
// Your WiFi credentials.
// Set password to "" for open networks.
char ssid[] = "YOUR_WIFI_SSID";
char pass[] = "YOUR_PASSWORD";
const char *host = "YOUR HOST";
const int httpsPort = 443; //HTTPS= 443 and HTTP = 80
//SHA1 fingerprint of certificate. Use your web browser to view the SHA1 fingerprint and copy
//Reply in this discussion if you don't know how to get the SHA1 fingerprint of your HTTPS website, thanks.
const char fingerprint[] PROGMEM = "AA BB 34 7B C0 FE CF 3C A8 2B 6D 31 6B 4B 9F C3 5B 6E A0 EE";
void setup()
{
// Debug serial console
Serial.begin(9600);
Blynk.begin(auth, ssid, pass);
timer.setInterval(1000L, myTimerEvent);
}
void loop()
{
Blynk.run();
timer.run();
}
void myTimerEvent()
{
WiFiClientSecure httpsClient; //Declare object of class WiFiClient
Serial.println(host);
Serial.printf("Using fingerprint '%s'\n", fingerprint);
httpsClient.setFingerprint(fingerprint);
httpsClient.setTimeout(15000); // 15 Seconds
delay(1000);
Serial.print("HTTPS Connecting");
int r = 0; //retry counter
while ((!httpsClient.connect(host, httpsPort)) && (r < 30))
{
delay(100);
Serial.print(".");
r++;
}
if (r == 30)
{
Serial.println("Connection failed");
}
else
{
Serial.println("Connected to web");
}
String Link;
Link = "/httpTest/?type=t"; // Here, the API for the Linux load averages are in the httpTest directory
Serial.print("requesting URL: ");
Serial.println(host + Link);
httpsClient.print(String("GET ") + Link + " HTTP/1.1\r\n" +
"Host: " + host + "\r\n" +
"Connection: close\r\n\r\n");
Serial.println("request sent");
while (httpsClient.connected())
{
String line = httpsClient.readStringUntil('\n');
if (line == "\r")
{
Serial.println("headers received");
break;
}
}
Serial.println("reply was:");
Serial.println("==========");
String line;
while (httpsClient.available())
{
line = httpsClient.readStringUntil('\n'); //Read Line by Line
Serial.println(line); //Print response
}
Serial.println("==========");
Serial.println("closing connection");
// crude way to parse string - should convert to json later
int ind1 = line.indexOf(':'); //finds location of first :
String l1 = line.substring(0, ind1); //captures first data String
int ind2 = line.indexOf(':', ind1 + 1); //finds location of second :
String l5 = line.substring(ind1 + 1, ind2 + 1); //captures second data String
int ind3 = line.indexOf(':', ind2 + 1); //finds location of third :
String l15 = line.substring(ind2 + 1, ind3 + 1); //captures second data String
l1.replace(":", "");
l5.replace(":", "");
l15.replace(":", "");
Blynk.virtualWrite(V0, l1.toFloat());
Blynk.virtualWrite(V1, l5.toFloat());
Blynk.virtualWrite(V2, l15.toFloat());
}
Here is the very simple service side PHP code.
This PHP code defaults to JSON, but the Arduino sketch above uses a crude "string" method, so the type is set to "t" in the code.
I suggest you add some filtering on the $_REQUEST and maybe some basic security (authorization key) if you go beyond the testing phase. Set the logging to match your preferred logging path.
This API is so simple, I don't think anyone really needs it.... but I include it for completeness:
<?php
http_response_code(200);
$type = $_REQUEST['type'];
$load = shell_exec('cat /proc/loadavg');
$pieces = explode(" ", $load);
if ($type == 't') {
$output = $pieces[0] . ":" . $pieces[1] . ":" . $pieces[2] . ":";
} else {
$output = '{"load1":"' . $pieces[0] . '","load5","' . $pieces[1] . '","load15","' . $pieces[2] . '"}';
}
error_log("Time: " . time() . " IP: " . $_SERVER['REMOTE_ADDR'] . " " . $output . "\n\n", 3, '/path/to/your/debuglog/esp8266_debug.log');
echo $output;
Basically, you will need to set up three Blynk gauges based on your visual and font size preferences, etc. There are many Blynk tutorials on the net, so I'll not repeat all those basic steps here unless anyone asks ![]()
If anyone would like to rewrite the API reply parser or modify to add the ArduinoJSON parser, please do so and post your code back.
Thanks.
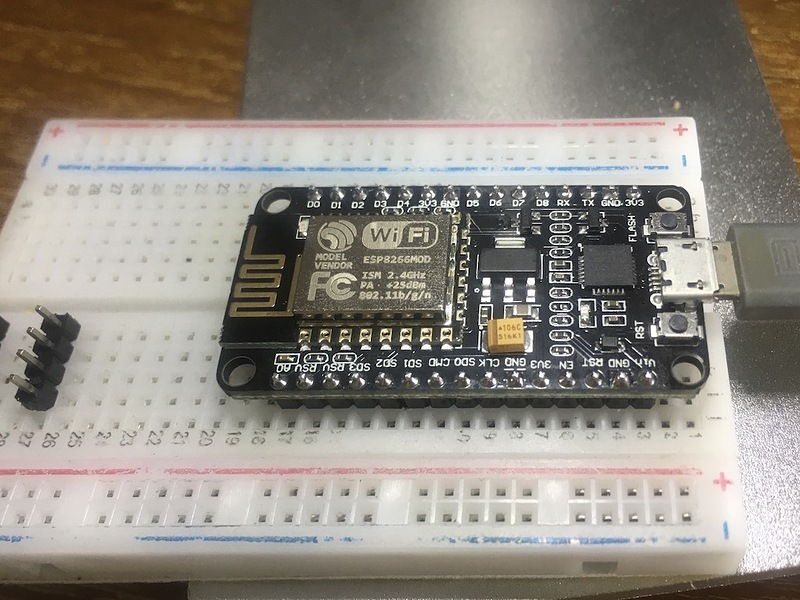

 LOL . Normally I am not really into home automation and surveillance apps (been there and done that a decade, maybe two, ago), but this ESP8266 is really amazing combined with the Arduino IDE for programming. They are so cheap, the sky is the limit!
LOL . Normally I am not really into home automation and surveillance apps (been there and done that a decade, maybe two, ago), but this ESP8266 is really amazing combined with the Arduino IDE for programming. They are so cheap, the sky is the limit!